Public-key Encryption
What is public-key encryption
definition & history
Each party has a pair(
is the public key, and used for encryption is the private key, and used for decryption - Satisfies
Secure Public Key encrytion is impossible when P=NP.(ref NP Theory)
Proposed by Diffie and Hellman, documented in "New Directions in Cryptography" (1976):
- Public-key encryption schemes
- Key distribution systems
- Digital signature
public key encryption algorithm
- RSA: based on the hardnesss of factoring large numbers
- EIGamal: based on the hardness of solving discrete algorithm
Diffie-Hellman Key Agreement Protocol
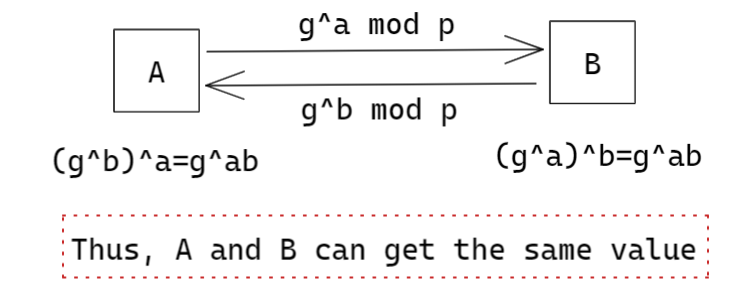
Security of DH is based on Three Hard Problems
- Discrete Log Problem(DLG)
- Computational Diffies Hellman Problem(CDH)
- Decision Diffie Hellman Problem(DDH)
EIGamal Encryption
- Public Key
- Private key is
- To encrypt message
: choose random , computes - To decrypt message
: , find which satisfies , thus
RSA Algorithm
Invented in 1978 by Ron Rives, Adi Shamir and Leonard Adleman
Key generation
- Select 2 large prime numbers of about the same size, p and q
- Compute
, and - Select
, , and are coprime - Determine
as (mod )
Encryption
Decryption
RSA security
- the length of
reflects the strength - Factoring is easy to break with quantum computers
- plain RSA does not provide IND-CPA security
Usage
- Often used to encrypt a symmetric key
- Signature(reverse usage)
ECC Algorithm
Digital Signatures
definition
signatures provide non-repudiation
- MAC: One party generated MAC, one party verifies integrity(one to one)
- Digital signatures: One party generates signature, many parties can verify(one to many)
- Digital signature scheme
- a signing algorithm: takes a message and a (private) signing key, outputs a signature.
- a verification algorithm: takes a (public) verification key, am essage and a signature.
- It provides
- Authentication
- Data integrity
- Non-Repudiation
RSA Signatures
- Public key(e, n): used for verification
- Private key(d): used for generation